Are you guys getting bored from your Old Whatsapp which give you simple as it is theme from day one & same emotions?
Try New WhtasApp Plus which give you 100 of New Themes as well as new emotions.
The best messaging and the most popular IM app now has multifarious
replacements. WhatsApp is already facing a tough competition from other IM apps, and now we bring to you, Whatsapp+.
To Download Click On " WhatsApp Plus " From Their Official Site Only

What is New features in WhatsApp Plus APK?
Whatsapp+ is a mod of Whatsapp by XDA developer rafalense.
WhatsApp+ allows users to modify and theme WhatsApp in ways not
achievable on the original Whatsapp application – for example, you can
hide your last seen status. Additionally, WhatsApp+ circumvents
many functional barriers in WhatsApp to give you a better overall
experience. For eg, no more image quality reduction when sending files.
Hide your last seen with WhatsApp+
Of course, since WhatsApp is a propriety application, the company has
sent a DMCA takedown notice to WhatsApp+. Fortunately, it is still
available online. So is WhatsApp+ really as good as it sounds? We find
out -
Special Features:
- Image quality has always been an issue with WhatsApp. While higher quality images are reduced in quality and size in the old WhatsApp, the new one does not face any such problem. Go ahead, share high quality pictures with your friends!
- The media sharing default limit is set to 16 MB in WhatsApp+ and can be increased till 50 MB. This new setting is an advantage over the old WhatsApp, whose media uploading limit was only 12 MB.
- Bored of refreshing your contact list and then clicking on your friend’s contact to see their current status? Well, WhatsApp+ frees you of this extra work by showing your contact’s status right below the chat.
- The green colour of the WhatsApp icon no longer seems appealing to you? Change the colour of the WhatsApp+ icon from its default blue to red, cyan, pink, gray, orange. And if you miss the original WhatsApp icon, you can change it to green again !
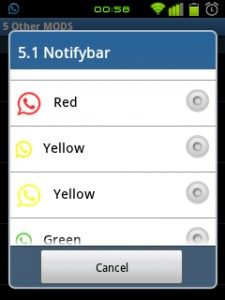
- There are innumerable themes which you can download in WhatsApp+ which wasn’t the case with the previous WhatsApp.
- You can attach your location, send voice messages and send or forward multiple messages.
No image quality reduction when you send files on WhatsApp+
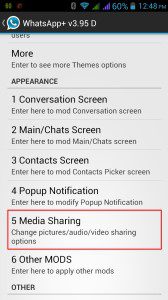
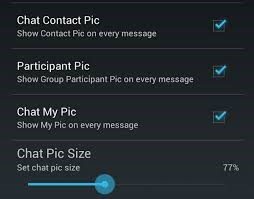

- You can modify the entire look of your chat screen, main screen, conversation screen, header background , contact icons. You can round up the corners of your contact pictures, change the colour of the chats, modify chat headers and rows, contacts headers and rows, change the colour of the notify bar and a lot more. You can personalise this app completely according to your choice.

- Like Hike, you can hide your online status in WhatsApp+. Though this is a paid service for which you need to download Plus Donation app from Play Store.
Verdict
NOT available on the Play Store
Since it is an unofficial mod, WhatsApp+ app is NOT available on Play
Store. Consequently, it faces stability issues on many devices. The app
is known to crash from time to time. This remains the biggest put-off
for the app, which if fixed, would ensure much higher downloads. You can
download it from 3rd party sites. The download should be an apk file
which you can install directly on your phone once transfer.
Caution: The original WhatsApp must be uninstalled
before you install WhatsApp+. Your conversations will automatically be
restored when you install WhatsApp Plus.
Attractive and appealing, with an interface which can be totally
modified according to the preferences of the user, for me WhatsApp Plus
is a sure shot replacement for the original WhatsApp.












